🤖 AI-Generated Content
This content has been created using artificial intelligence. While we strive for accuracy, please verify important information independently.
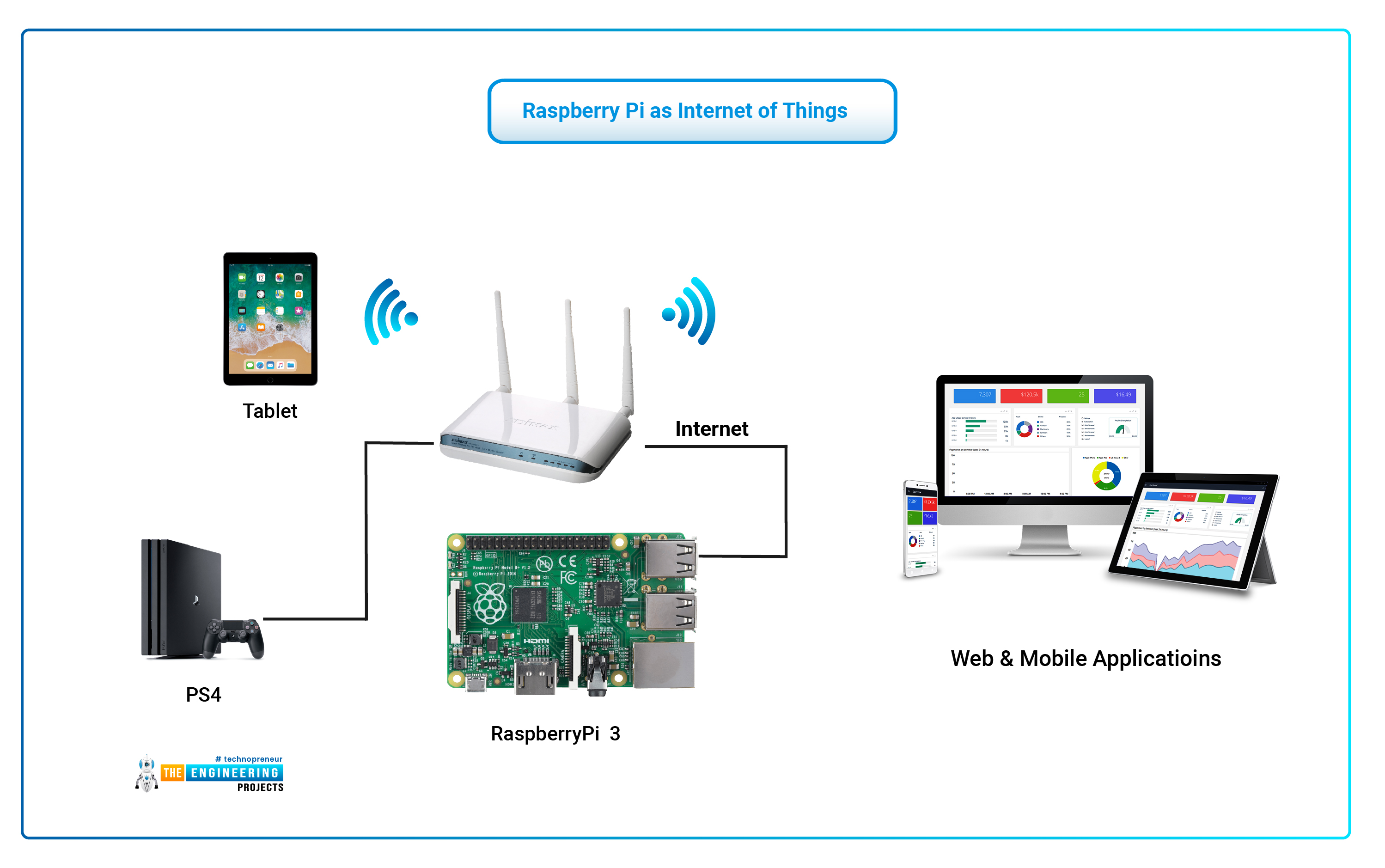
Imagine, if you will, a small computer, perhaps a Raspberry Pi, sitting quietly in your home. It's connected to your local network, doing its thing, maybe running some clever little automation or collecting bits of information. Now, picture yourself far away from home, perhaps on a trip or just at a friend's place. You suddenly have a thought: "I need to check on that device," or "I want to make it do something right now!" This is where things can get a little tricky, you know, because that little computer is tucked away behind your home's main internet gateway, the router. It's almost like it's in its own private club, and getting in from the outside takes a special kind of invitation.
Connecting to devices that are inside your home network, especially when you are not there, presents a common puzzle for many folks who enjoy tinkering with small computers. These devices, like a Raspberry Pi, typically get a private address from your router, which means they are not directly visible to the wider internet. So, if you want to give instructions to your Raspberry Pi, or perhaps gather some data from it, while you are miles away, you cannot just type in its usual local address. It's a bit like trying to call someone who only has an internal office extension number from outside the building; you need a way to bridge that gap, you know.
The good news is that there are some clever methods people use to make this kind of remote access possible. We are going to talk about how you can make your Raspberry Pi, which is a very popular choice for these kinds of projects, reachable even when it's sitting behind your router. This discussion will give you a clear remoteiot behind router example in raspberry pi, showing you how to set up a way to communicate with your device, giving you control no matter where you are. It’s actually quite a neat trick, if you ask me.
Table of Contents
- What Does "Behind a Router" Really Mean?
- Why Can't I Just Connect to My Raspberry Pi?
- Getting Ready- Your Raspberry Pi for Remote Access
- How Do People Usually Reach Devices Like This?
- Setting Up a Reverse SSH Tunnel - A Practical RemoteIoT Behind Router Example in Raspberry Pi
- What About Security When You Have RemoteIoT Behind Router Example in Raspberry Pi?
- Are There Other Ways to Get Your RemoteIoT Behind Router Example in Raspberry Pi Online?
- Everyday Uses for a Remotely Accessible Raspberry Pi
What Does "Behind a Router" Really Mean?
When we talk about a device being "behind a router," we are describing its position within a typical home or small office network setup. Think of your router as a kind of front door for your entire home network. All the devices inside your house, like your smart TV, your phone, your laptop, and of course, your Raspberry Pi, are on the "inside" of this door. They communicate with each other using private addresses, which are numbers that only make sense within your home's network. For example, your Raspberry Pi might have an address like 192.168.1.100. This address is essentially a local extension number, you know, only usable within your home.
The router itself has two main types of addresses. It has a private address for talking to devices inside your home, and it also has a public address, which is the one the outside world sees. This public address is given to your router by your internet service provider. So, when you visit a website, your request goes from your device, through your router, and then out to the internet using your router's public address. The replies come back to your router, and it then directs them to the correct device inside your home. This setup is very common, and it is actually a good thing for security, as a matter of fact.
For a remoteiot behind router example in raspberry pi, this means your little computer is not directly exposed to the wide-open internet. It is protected by your router's built-in defenses, which usually block any incoming connections from the outside unless you specifically tell the router to allow them. This makes it a very safe way to operate your devices locally, but it does create a hurdle when you want to reach them from somewhere far away. It is like having a private conversation in your living room; people outside cannot just listen in.
- Jameliz Benitez Leaked
- Yemada Onlyfans
- Wasmo Telegram Link 2025
- Piper Rockelle Ai Nudes
- Jules Ari Onlyfans Leaks
Why Can't I Just Connect to My Raspberry Pi?
You might wonder, why can't I just type in my Raspberry Pi's local address when I am away from home? The answer lies in how home networks manage their connections to the broader internet. Your router performs a task called Network Address Translation, or NAT for short. This is basically a system where your router takes all the private, local addresses from your home devices and translates them into its single public address when communicating with the outside world. When information comes back, it reverses the process, sending the data to the right local device. It is a bit like a post office that sorts mail for everyone in an apartment building, you know, ensuring each letter gets to the correct resident even though the building only has one street address.
Because of NAT, when you try to connect to your home network from the outside, the internet only sees your router's public address. It does not know about the individual private addresses of your devices, like your Raspberry Pi. The router, by its very design, usually blocks unsolicited incoming connections from the internet. This is a fundamental security feature. It prevents random people or programs from the internet from simply "knocking" on the virtual doors of your internal devices. So, if you are looking for a remoteiot behind router example in raspberry pi, you will find that this security measure is the very reason you cannot just connect directly.
Think of it this way: your router is like a very cautious doorman. It lets people inside your building make calls out, and it knows where to send replies back to them. But if someone from the outside tries to call an internal extension directly, the doorman just says, "Sorry, that number is not public." This protection is good, of course, because it keeps your home network more secure from unwanted visitors. However, it also means you need a specific strategy to get past this doorman when you actually want to reach your Raspberry Pi from afar. It is not impossible, just different, you know.
Getting Ready- Your Raspberry Pi for Remote Access
Before you even think about connecting to your Raspberry Pi from a distance, you need to make sure it is set up properly on your home network. This initial preparation is quite important for any remoteiot behind router example in raspberry pi. First, ensure your Raspberry Pi is connected to your router, either with a network cable or through Wi-Fi. It is generally a good idea to give your Raspberry Pi a static local IP address. This means its address on your home network will not change, which makes it much easier to find consistently. You can usually set this up in your router's settings or directly on the Raspberry Pi itself.
Next, you will want to make sure your Raspberry Pi's software is all up to date. This is a good practice for security and stability, you know. You can do this by opening a terminal on your Pi and running a couple of simple commands. It just helps everything work smoothly when you try to connect from somewhere else. Also, for many remote connection methods, you will need to have SSH, which stands for Secure Shell, enabled on your Raspberry Pi. SSH is a way to securely access the command line of your Pi from another computer. It is usually enabled by default on newer Raspberry Pi operating systems, but it is always good to check.
To check if SSH is enabled, or to turn it on, you can use the Raspberry Pi Configuration tool, which is a graphical interface, or you can use a command in the terminal. If you are going to use SSH, it is also very important to change the default password for the 'pi' user, or even better, set up SSH key-based authentication. This makes your connection much more secure, as a matter of fact. These simple steps lay the groundwork for any successful remoteiot behind router example in raspberry pi, making sure your device is ready to communicate with the outside world on your terms.
How Do People Usually Reach Devices Like This?
Since directly connecting to a device behind a router is not really an option, people have come up with several clever ways to get around this. Each method has its own set of things to consider, but they all aim to solve the same problem: making your private device accessible from the public internet, but only in a controlled way. When you are thinking about a remoteiot behind router example in raspberry pi, you will often hear about a few main strategies.
One common method is called "port forwarding." This is where you tell your router to send specific incoming connections from the internet to a particular device on your home network. For example, you might tell your router that any connection trying to reach port 22 (which is usually for SSH) should be sent directly to your Raspberry Pi's private IP address. While this works, it does mean you are opening a specific "door" in your router to the internet, which some people feel is a bit risky if not done carefully. It exposes that particular port to the whole internet, you know.
Another approach involves setting up a Virtual Private Network, or VPN. In this setup, your Raspberry Pi or another device on your home network acts as a VPN server. When you are away, your remote device connects to this VPN server, creating a secure, encrypted tunnel. Once connected, your remote device essentially becomes part of your home network, allowing you to access your Raspberry Pi as if you were sitting right there in your living room. This is a very secure method, but it can be a bit more involved to set up, especially if your router does not support VPN server functions directly. For a remoteiot behind router example in raspberry pi, this can be a solid, if slightly complex, choice.
Then there is the "reverse SSH tunnel," which is a really neat trick. Instead of you trying to connect into your home network, your Raspberry Pi initiates an outgoing connection to a public server that you control. This connection then creates a "tunnel" back into your Raspberry Pi. Because the connection is initiated from the inside out, your router sees it as a regular outgoing connection and does not block it. You can then connect to your public server, and through that server, you can reach your Raspberry Pi. This is often preferred because it does not require changing your router's settings for port forwarding, which is a nice benefit, actually.
Finally, there are cloud-based IoT platforms. These services act as a middleman. Your Raspberry Pi connects to the cloud platform, and then you, from your remote location, also connect to the same platform. The platform then facilitates communication between you and your Raspberry Pi. This often simplifies the setup process quite a bit, as the cloud service handles many of the network connection complexities. While it might involve a subscription fee for some features, it can be a very convenient way to manage a remoteiot behind router example in raspberry pi without getting too deep into network configurations.
Setting Up a Reverse SSH Tunnel - A Practical RemoteIoT Behind Router Example in Raspberry Pi
Let us look a little closer at setting up a reverse SSH tunnel, as this is a very effective and widely used method for reaching devices behind a router without needing to mess with port forwarding. The basic idea here is that your Raspberry Pi, which is inside your home network, will make an outgoing connection to a publicly accessible server somewhere on the internet. This connection then forms a secure pathway, or "tunnel," back to your Raspberry Pi. Think of it like your Pi calling a friend's phone and leaving the line open, so the friend can then use that open line to talk back to your Pi, even though your Pi is behind a private number.
To make this work, you will need two main things: your Raspberry Pi, of course, and a public server. This public server could be a very small, inexpensive virtual private server (VPS) that you rent from a cloud provider. It just needs to have a public IP address and be able to accept incoming SSH connections. Many people use a simple Linux server for this, which is quite common. For our remoteiot behind router example in raspberry pi, this public server acts as the meeting point.
First, on your public server, you need to make sure SSH is running and that it allows "GatewayPorts." This setting tells the SSH server that it is okay to forward connections that come in from outside. You usually adjust a line in the SSH server's configuration file for this. It is a pretty straightforward change, actually. Once that is done, your public server is ready to listen for the incoming tunnel request from your Raspberry Pi.
Next, you will configure your Raspberry Pi. The command to create the reverse tunnel is executed on the Raspberry Pi itself. It tells the Pi to connect to your public server and, while doing so, to create a specific port on the public server that will "tunnel" back to a specific port on your Raspberry Pi. For instance, you might tell the public server to open port 8080, and any connection to 8080 on the public server will be sent back through the tunnel to port 22 (SSH) on your Raspberry Pi. This is how you effectively bypass your home router's blocking of incoming connections.
A typical command might look something like this: `ssh -N -R 8080:localhost:22 user@your_public_server_ip`. Let us break that down a little. `-N` means "do not execute a remote command," which is just for setting up the tunnel. `-R` indicates a reverse port forward. `8080` is the port on the public server that will be opened. `localhost:22` refers to the Raspberry Pi's own SSH port. And `user@your_public_server_ip` is how your Pi connects to your public server. Once this command runs on your Pi, the tunnel is established.
To keep the tunnel active, especially if the connection drops, people often use tools like `autossh` or set up a system service that automatically restarts the SSH command if it stops running. This ensures that your remoteiot behind router example in raspberry pi remains accessible consistently. Once the tunnel is up, you can then SSH into your public server, and from there, connect to your Raspberry Pi through the forwarded port. So, if your public server's IP is `123.45.67.89`, you would SSH to it, and then from within that server, you could connect to your Pi using `ssh pi@localhost -p 8080`. It is a very effective way to bridge the gap.
What About Security When You Have RemoteIoT Behind Router Example in Raspberry Pi?
When you start making your devices accessible from outside your home network, even with clever methods like reverse SSH tunnels, thinking about security becomes really important. You are, in a way, creating a path into your home network, and you want to make sure only the people you want to have access can use that path. This is a very big deal for any remoteiot behind router example in raspberry pi, you know.
First, always use strong passwords. This might seem like a very basic piece of advice, but it is often overlooked. For your Raspberry Pi, make sure the default 'pi' user password is changed to something long and complex. For your public server, the same rule applies. Even better than passwords, use SSH key pairs for authentication. This involves generating a pair of cryptographic keys: a private key that stays on your computer and a public key that you put on your Raspberry Pi and your public server. When you try to connect, the keys are used to verify your identity, which is much more secure than a password that could be guessed or stolen.
Also, consider limiting who can log in to your Raspberry Pi and your public server. If you only need one user account for remote access, disable password login for other accounts. You can also configure your SSH server to only allow connections using key pairs, completely turning off password authentication. This makes it much harder for someone to gain unauthorized access, as a matter of fact.
Keep your software updated. This includes the operating system on your Raspberry Pi and on your public server, as well as any applications you are running. Software updates often include security fixes that address newly discovered vulnerabilities. Running outdated software is like leaving a window open for potential problems. Regularly checking for and applying updates is a simple yet very effective way to maintain the safety of your remoteiot behind router example in raspberry pi setup.
Finally, only open the ports you absolutely need on your public server. If you are using a reverse SSH tunnel, you are only forwarding one or two ports. Make sure your public server's firewall is set up to only allow incoming connections on those specific ports and perhaps the standard SSH port (22) for your own management access. Blocking all other ports reduces the "attack surface" and makes your server much harder to compromise. It is all about being careful and thoughtful with your setup, basically.
Are There Other Ways to Get Your RemoteIoT Behind Router Example in Raspberry Pi Online?
While the reverse SSH tunnel is a really powerful and flexible way to reach your Raspberry Pi from afar, it is not the only option. As we touched on earlier, cloud-based IoT platforms offer a different path, and they can be very appealing, especially if you want to avoid some of the more hands-on network setup. These platforms are designed specifically for connecting and managing a large number of internet-connected devices, including things like a remoteiot behind router example in raspberry pi.
How do they work? Basically, your Raspberry Pi runs a small piece of software, sometimes called an agent or SDK, that connects to the cloud platform over the internet. This connection is always initiated from the Raspberry Pi itself, so your home router sees it as an outgoing connection and does not block it. Once connected, your Pi registers itself with the cloud service. Then, when you want to interact with your Pi, you log into the same cloud platform from your web browser or a mobile app. The platform then acts as a secure intermediary, sending your commands to your Raspberry Pi and receiving data back from it.
One of the big benefits of using these services is that they handle much of the underlying network complexity for you. You do not typically need to worry about static IP addresses, port forwarding, or setting up your own public server. The cloud provider takes care of all that infrastructure. They also often provide ready-made tools for managing your devices, sending commands, collecting data, and even visualizing that data. This can make the process of getting your remoteiot behind router example in raspberry pi up and running much quicker and simpler, particularly for those who are not deeply familiar with network administration.
However, there are a few things to keep in mind. Many of these services operate on a subscription model, so there might be ongoing costs, especially if you have many devices or generate a lot of data. Also, you are relying on a third-party service, so you need to be comfortable with your device's data flowing through their systems. For some projects, the simplicity and features offered by these platforms definitely outweigh these considerations, making them a very practical choice. It really depends on your specific needs and comfort level with different approaches, you know.
Everyday Uses for a Remotely Accessible Raspberry Pi
Once you have successfully set up a way to reach your Raspberry Pi from anywhere, the possibilities for what you can do with a remoteiot behind router example in raspberry pi really open up. It moves your little computer from being just a local gadget to a truly global tool, ready to respond to your commands or send you information no matter where you are.
Think about home automation, for instance. You could have your Raspberry Pi controlling smart lights, monitoring indoor temperature, or even managing your garden's watering system. With remote access, you could check the temperature from your phone while on vacation and turn on the fan if it is too warm. Or, you could activate your sprinklers if you see that your plants are looking a little thirsty, even if you are miles away. It is pretty cool, actually, having that kind of control.
Additional Resources
Visual Content


Disclaimer: This content was generated using AI technology. While every effort has been made to ensure accuracy, we recommend consulting multiple sources for critical decisions or research purposes.
